FedRAMP Authorization
360 Advanced offers FedRAMP authorization services, beginning with a thorough gap assessment to evaluate architecture, documentation, and policies against FedRAMP requirements. We analyze data and business objectives to define an implementation roadmap tailored to the client’s needs, whether through JAB or Agency-sponsored pathways.
We conduct independent assessments, including penetration testing, manual security control tests, and vulnerability scanning, compiling all documentation into a comprehensive Security Assessment Report (SAR) and assessment package. Through our expertise, we guide clients towards successful certification and enhanced security in the federal cloud computing landscape.
What is FedRAMP?
The Federal Risk and Authorization Management Program, FedRAMP, promotes the adoption of secure cloud services across the U.S. government, providing a standardized approach to security assessments for cloud service offerings. FedRAMP creates a partnership between the federal government and industry. Together, we modernize IT infrastructure while protecting federal information.
FedRAMP is based on the National Institute of Standards and Technology (NIST) Special Publication (SP) 800-53 Security and Privacy Controls, as well as low/moderate categorization of Federal Information Processing Standard 199 (FIPS 199). SP800-53 is the control set that is used by federal agencies themselves to meet the FISMA regulations and is currently being updated to revision 5. The Federal information Processing Standard (FIPS 199) is the standard for document processing, encryption algorithms and other information technology standards for use within non-military government agencies and by government contractors and vendors. FedRAMP standards are more stringent than NIST.
Before FedRAMP, vendors had to meet different security requirements for each federal agency. FedRAMP eliminates this duplication by providing a common security framework, making it possible for agencies and cloud service providers to reuse authorizations. Agencies review a standardized set of security materials against one common baseline. A cloud service offering is authorized once and then the security package can be used by any federal agency.
Our Services
Gap Assessment
- Capture current state of architecture, documentation, policies and procedures, through virtual workshops with key stakeholders to assess gap against FedRAMP requirements
- Analyze data, users and use cases to categorize system sensitivity based on FIPS 199 to define applicable FedRAMP or DOD RMF requirements and define architecture impact e.g. using AWS East/West versus AWS GovCloud
- Review and analyze business objectives including target markets, timelines and budgetary considerations to define an implementation roadmap and FedRAMP ATO pathway e.g. JAB versus Agency-sponsored
- Management briefing to walk through findings, recommendations, and a proposed implementation plan with actionable next steps
Independent Assessment
- Project Plan: Develop an assessment project plan
- Security Assessment Plan (SAP): Draft a SAP outlining security controls selected for the assessment and all the testing methodologies as applicable to the operating environment
- Rules of Engagement: Set rules of engagement identifying the methodology, approach, include/exclude target list, tools employed, key personnel, and escalation information for all vulnerability scanning activities
- Penetration Test: Conduct a Penetration Test in accordance with FedRAMP assessment requirements and include results in the Security Assessment Report (SAR)
- Security Control Tests: Conduct manual security control tests using the FedRAMP Test Case Workbook in accordance with the testing procedures and guidance in NIST SP 800-53A, Rev 4
- Artifacts: Maintain an organized file of all collected evidence for each test case or control
- FedRAMP Test Cases: Records all manual test results in a Security Requirements Traceability Matrix (SRTM) with evidence artifacts mapped to each test case or control
- Vulnerability Scanning: Conduct automated vulnerability scanning and obtain, review, analyze, and compile results
- Security Assessment Report (SAR): Develop a SAR outlining the system overview, assessment methodology, assessment results, analysis of non-conforming controls, risk assessment of findings, authorization recommendation, and necessary attachments
- Assessment Package: Provide final assessment package
Oversight
FedRAMP is controlled by a Joint Authorization Board (JAB). The board is made up of representatives from:
- Department of Homeland Security
- General Services Administration (GSA)
- Department of Defense (DoD)
The program is endorsed by the U.S. Government Federal Chief Information Officers Council.
FedRAMP’s guiding principle is reuse: do once, use many times. This saves money, time, and effort for both agencies and Cloud Service Providers.
Importance of FedRAMP Certification
All cloud services holding federal data require FedRAMP authorization. So, if you want to work with the federal government, FedRAMP authorization is an important part of your security plan. FedRAMP is important because it ensures consistency in the security of the government’s cloud services—and because it ensures consistency in evaluating and monitoring that security. It provides one set of standards for all government agencies and all cloud providers.
Cloud service providers that are FedRAMP authorized are listed in the FedRAMP Marketplace. This marketplace is the first-place government agencies look when they want to source a new cloud-based solution. It is much easier and faster for an agency to use a product that’s already authorized than to start the authorization process with a new vendor.
A listing in the FedRAMP marketplace makes you much more likely to get additional business from government agencies, and it can also improve your profile in the private sector. The FedRAMP marketplace is visible to the public, and any private sector company can scroll through the list of FedRAMP authorized solutions.
FedRAMP authorization can make any client more confident about the security protocols in place. It represents an ongoing commitment to meeting the highest security standards. Additionally, FedRAMP authorization significantly boosts your security credibility beyond the FedRAMP Marketplace.
What Does It Take to be Certified?
1. Joint Authorization Board (JAB) Provisional Authority to Operate
In this process, the JAB issues a provisional authorization. That lets agencies know the risk has been reviewed. It is an important first approval, but any agency that wants to use the service still must issue their own Authority to Operate. This process is best suited for cloud services providers with high or moderate risk.

2. Agency Authority to Operate
In this process, the cloud services provider establishes a relationship with a specific federal agency. That agency is involved throughout the process. If the process is successful, the agency issues an Authority to Operate letter.
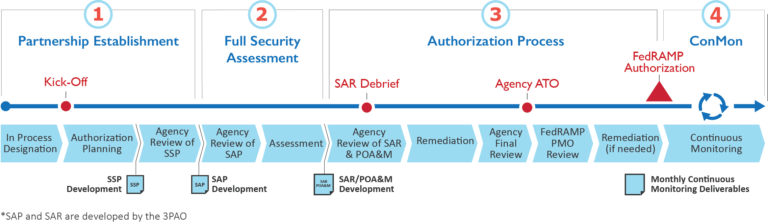
Steps to Authorization
No matter which type of authorization you pursue, FedRAMP authorization involves four main steps:
-
-
- Package Development. First, there is an authorization kick-off meeting. Then the provider completes a System Security Plan (SSP). Next, a FedRAMP-approved third-party assessment organization develops a Security Assessment Plan (SAP).
- The Assessment Organization submits a Security Assessment report (SAR). The provider creates a Plan of Action & Milestones (POAM).
- The JAB or authorizing agency decides whether the risk as described is acceptable. If yes, they submit an Authority to Operate (ATO) letter to the FedRAMP project management office. The provider is then listed in the FedRAMP Marketplace.
- The Provider sends monthly security monitoring deliverables to each agency using the service.
-
Impact Levels of FedRAMP
FedRAMP offers four impact levels for services with different kinds of risk. They’re based on the potential impacts of a security breach in three different areas.
-
-
- Confidentiality: Protections for privacy and proprietary information.
- Integrity: Protections against modification or destruction of information.
- Availability: Timely and reliable access to data.
-
The first three impact levels are based on Federal Information Processing Standard (FIPS) 199 from the National Institute of Standards and Technology (NIST). The fourth is based on NIST Special Publication 800-37. The impact levels are:
-
-
- High, based on 421 controls. “The loss of confidentiality, integrity, or availability could be expected to have a severe or catastrophic adverse effect on organizational operations, organizational assets, or individuals.” This usually applies to law enforcement, emergency services, financial, and health systems.
- Moderate, based on 325 controls. “The loss of confidentiality, integrity, or availability could be expected to have a serious adverse effect on organizational operations, organizational assets, or individuals.” Nearly 80 percent of approved FedRAMP applications are at the moderate impact level.
- Low, based on 125 controls. “The loss of confidentiality, integrity, or availability could be expected to have a limited adverse effect on organizational operations, organizational assets, or individuals.”
- Low-Impact Software-as-a-Service (LI-SaaS), based on 36 controls. For systems that are low risk for uses like collaboration tools, project management applications, and tools that help develop open-source code. This category is also known as FedRAMP Tailored. To qualify for FedRAMP Tailored, the provider must answer yes to these six questions:
-
- Does the service operate in a cloud environment?
- Is the cloud service fully operational?
- Is the cloud service a Software as a Service (SaaS), as defined by NIST SP 800-145, The NIST Definition of Cloud Computing?
- The cloud service does not contain personally identifiable information (PII), except as needed to provide a login capability (username, password and email address)?
- Is the cloud service low-security-impact, as defined by FIPS PUB 199, Standards for Security Categorization of Federal Information and Information Systems?
- Is the cloud service hosted within a FedRAMP-authorized Platform as a Service (PaaS) or Infrastructure as a Service (IaaS), or is the CSP providing the underlying cloud infrastructure?
-
-
IaaS vs. PaaS vs. SaaS
NIST SP 800-145 establishes FedRAMP’s definitions for cloud services that are IaaS, PaaS, or SaaS. CSPs needing to define their offerings as one or multiple of the service models should refer to the following guidelines:
Software-as-a-Service (SaaS): The capability provided to the consumer is to use the provider’s applications running on a cloud infrastructure. The applications are accessible from various client devices through either a thin client interface, such as a web browser (e.g., web-based email), or a program interface. The consumer does not manage or control the underlying cloud infrastructure, including network, servers, operating systems, storage, or even individual application capabilities, apart from limited user-specific application configuration settings.
Platform-as-a-Service: The capability provided to the consumer is to deploy consumer-created or acquired applications created using programming languages, libraries, services, and tools supported by the provider onto the cloud infrastructure. The consumer does not manage or control the underlying cloud infrastructure, including network, servers, operating systems, or storage, but has control over the deployed applications and possibly configuration settings for the application-hosting environment.
Infrastructure-as-a-Service: The capability provided to the consumer is to provide processing, storage, networks, and other fundamental computing resources where the consumer is able to deploy and run arbitrary software, which can include operating systems and applications. The consumer does not manage or control the underlying cloud infrastructure but has control over operating systems, storage, and deployed applications, and possibly limited control of select networking components.
FedRAMP Authorization Best Practices
-
-
- Understand how your product maps to FedRAMP – including a gap analysis.
- Get organizational buy-in and commitment – including from the executive team and technical teams.
- Find an agency partner – one that is using your product or is committed to doing so.
- Spend time accurately defining your boundary. That includes:
-
-
- Internal components
- Connections to external services, and
- the flow of information and metadata.
-
-
- Think of FedRAMP as a continuous program, rather than just a project with a start and end date. Services must be continuously monitored.
- Carefully consider your authorization approach. Multiple products may require multiple authorizations.
- The FedRAMP PMO is a valuable resource. They can answer technical questions and help you plan your strategy.
-
